Conócenos
Objetivos
Objetivo general
El objetivo de la Sección de Estudios de Posgrado e Investigación de la ESIME Culhuacan es formar egresados de nivel posgrado, capaces de entender las problemáticas y aspectos en el área de ingeniería para poder vincularse con el sector productivo, social y educativo, creando proyectos de investigación y desarrollo tecnológico, convirtiéndose en eje fundamental para el desarrollo educativo y tecnológico del país.
Objetivos particulares
Formar investigadores, altamente especializados que realicen investigación de frontera, docencia, consultoría y desarrollo tecnológico.
Ayudar a elevar la competitividad de las empresas nacionales, mediante el desarrollo de diversas líneas de investigación creando así un vínculo con el sector productivo y social.
Misión y visión
Misión
Es la de formar investigadores de especialidad, maestría y doctorado del más alto nivel, con un gran sentido de responsabilidad y valores bien fundamentados para coadyuvar a la sociedad y contribuir al desarrollo sustentable que el país requiere.
Visión
Ser uno de las mejores centros de estudios de posgrado e investigación del país y del mundo, incorporando y aplicando la técnica y la ciencia en la vida productiva y social del país.
Origen
Currículo del Jefe de la Sección de Estudios de Posgrado e Investigación
M. en C. Osvaldo López García.
Originario de la Ciudad de México, realizó sus estudios de nivel medio superior en el CECyT No. 4 “Lázaro Cárdenas del Rio” egresando con el título de Técnico en Electricidad (1991 a 1994), posteriormente ingresó a la ESIME Unidad Culhuacan para cursar sus estudios de nivel superior, obteniendo el título de Ingeniero en Comunicaciones y Electrónica, con especialidad en Comunicaciones (1994 a 2000). En la vida docente comenzó como profesor de la ESIME en la Academia de Comunicaciones de la carrera de Ingeniería en Comunicaciones y Electrónica en 2001. Ingresó al nivel posgrado en la SEPI Unidad Culhuacan perteneciendo a la tercera generación, obteniendo el grado de Maestro en Ciencias de Ingeniería en Microelectrónica en el 2003. Ingresó como funcionario público dentro de la administración en la ESIME Culhuacan como jefe del Departamento de Recursos Materiales durando en el puesto siete años, del 2005 al 2012. Posteriormente me incorporó como jefe del Departamento de Posgrado, durando en el puesto también siete años del 2012 al 2019. Finalmente el 01 de Noviembre lo designan como Jefe Interino de la SEPI Unidad Culhuacan el cual realiza con mucho entusiasmo y dedicación, pues es el primer jefe de Sección egresado de algún programa de esta Sección. La mayor satisfacción que le ha dado los puestos administrativos son el realizar distintas actividades dentro del Instituto conociendo mucha gente, la cual le ha dejado entre ellas muchas enseñanzas, pero sobre todo poner “La Técnica al Servicio de la Patria”.
Currículo de la Jefa del Departamento de Posgrado
M. en C. Nancy Mondragón Escamilla.
FORMACION:
- Maestría en Ciencias de Ingeniería en Microelectrónica
Sección Estudios de Posgrado e Investigación de la ESIME Culhuacan
2008-2010. Cédula Profesional: 7888252 - Ingeniería en Comunicaciones y Electrónica
Instituto Politécnico Nacional
Escuela Superior de Ingeniería Mecánica y Eléctrica
Unidad Culhuacan. 2002-2006. Cédula Profesional: 6004032 - Técnico en Electricidad
Centro de Estudios Tecnológicos Industrial y de Servicios No.39
1998-2001. Cédula Profesional: 4674725
Currículo de la Jefa del Departamento de Investigación
M. en I. Lidia Prudente Tixteco
Ingeniera en Computación, Especialista en Seguridad Informática y Tecnologías de la Información (ESITI) y Maestra en Ingeniería en Seguridad y Tecnologías de la Información (MISTI) por el Instituto Politécnico Nacional.
Desde hace más de 10 años docente de la ESIME Culhuacan del IPN en la Carrera de Ingeniería en Computación y a partir de 2015 en la MISTI de la Sección de Estudios de Posgrado e Investigación (SEPI) de la misma Unidad en la que ha impartido diversos cursos y asesorado proyectos de titulación u obtención de grado.
Desde 2016 ha dirigido Proyectos de Investigación Institucionales aprobados por la Secretaría de Investigación y Posgrado del IPN relacionados con temas de seguridad de la información, asimismo ha participado y dirigido proyectos de colaboración y capacitaciones de seguridad y auditoría entre Instituciones públicas y privadas y la ESIME Culhuacán.
En septiembre de 2020 fue nombrada Jefa del Departamento de Investigación de la SEPI en la ESIME Culhuacán.
Sus principales temas de interés son Gestión de la Seguridad de la Información y Ciberseguridad, Gestión de Riesgos en el Ciberespacio, Educación en Seguridad y Seguridad en Educación.
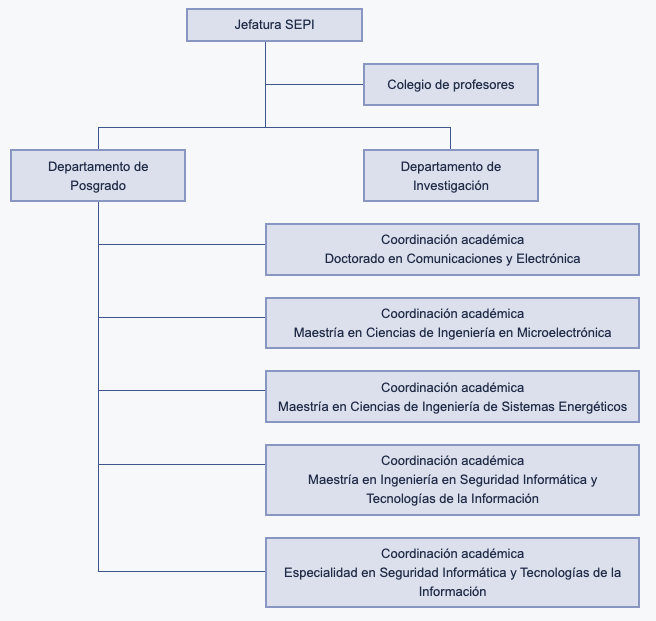
Organigrama
Ubicación
SEPI – ESIME Culhuacan
Edificio #2, 3er. Piso
Av. Sta. Ana 1000, San Francisco Culhuacán, Culhuacan CTM V, Coyoacán, 04440 Ciudad de México, CDMX










